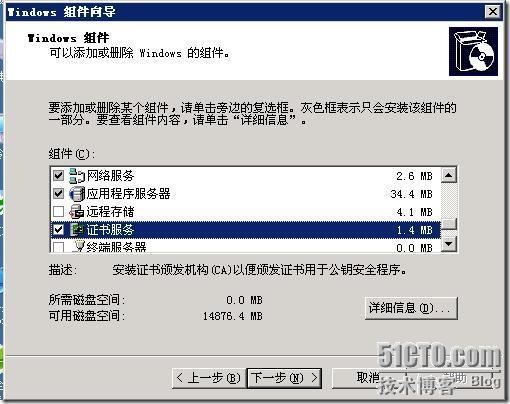
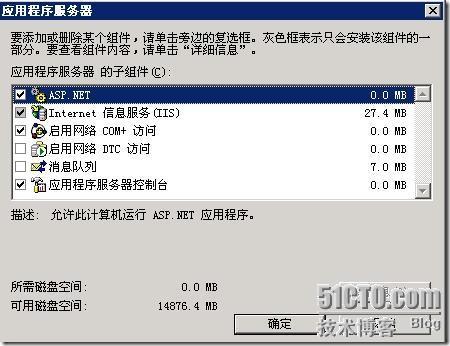
添加IIS:勾选“应用程序服务器”,然后双击进入下图,勾选“IIS”和“ASP.NET”添加证书系统:勾选“证书服务”
添加组件的时候要求填写的就按照操作填上就行了,然后下一步,直到完成。
Country Name: CN //两个字母的国家代号
State or Province Name: guang dong //省份名称
Locality Name: guang zhou //城市名称
Organization Name: sunrising //公司名称
Organizational Unit Name: home //部门名称
Common Name: besunny //你的姓名(要是生成服务器端的证书一定要输入域名或者ip地址)
Email Address: Email地址
copy cacert.pem demoCA
openssl ca -in certreq.txt -out server.pem -config d:\openssl-0.9.7\apps\openssl.cnf
openssl x509 -in server.pem -out server.cer
openssl req -newkey rsa:1024 -keyout clikey.pem -out clireq.pem -days 365 -config d:\openssl-0.9.7\apps\openssl.cnf
openssl ca -in clireq.pem -out client.crt -config d:\openssl-0.9.7\apps\openssl.cnf
openssl pkcs12 -export -clcerts -in client.crt -inkey clikey.pem -out client.p12 -config d:\openssl-0.9.7\apps\openssl.cnf
运行:cmd
(C) 版权所有 1985-2001 Microsoft Corp.
D:\openssl-0.9.7\out32dll> openssl req -x509 -newkey rsa:1024 -keyout cakey.pem
-out cacert.pem -days 3650 -config d:\openssl-0.9.7\apps\openssl.cnf
Loading 'screen' into random state - done
Generating a 1024 bit RSA private key
........++++++
..++++++
writing new private key to 'cakey.pem'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Beijing
Locality Name (eg, city) []:Beijing
Organization Name (eg, company) [Internet Widgits Pty Ltd]:ZZNODE
Organizational Unit Name (eg, section) []:DI
Common Name (eg, YOUR name) []:10.1.1.168
Email Address []:huangbili@263.net
改写 demoCA\private\cakey.pem 吗? (Yes/No/All): y
已复制 1 个文件。
改写 demoCA\cacert.pem 吗? (Yes/No/All): y
已复制 1 个文件。
Using configuration from D:\OpenSSL\bin\openssl.cnf
Loading 'screen' into random state - done
Enter pass phrase for ./demoCA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 286 (0x11e)
Validity
Not Before: Jan 20 16:20:51 2006 GMT
Not After : Jan 20 16:20:51 2007 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijing
organizationName = ZZNODE
organizationalUnitName = DI
commonName = 10.1.1.168
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
52:4A:01:08:B0:DD:5D:B1:48:46:CB:62:6F:31:CA:4D:8A:DA:6C:2F
X509v3 Authority Key Identifier:
keyid:A6:4E:E1:7D:EC:BF:59:33:1D:16:30:3B:F3:4B:D4:C8:CC:B5:0E:75
Sign the certificate? [y/n]:y
Write out database with 1 new entries
Data Base Updated
Loading 'screen' into random state - done
Generating a 1024 bit RSA private key
........................................................................++++++
.........................++++++
writing new private key to 'clikey.pem'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:Beijing
Locality Name (eg, city) []:Beijing
Organization Name (eg, company) [Internet Widgits Pty Ltd]:ZZNODE
Organizational Unit Name (eg, section) []:DI
Common Name (eg, YOUR name) []:huangbl
Email Address []:huangbili@263.net
to be sent with your certificate request
A challenge password []:test
An optional company name []:ZZNODE
Using configuration from D:\OpenSSL\bin\openssl.cnf
Loading 'screen' into random state - done
Enter pass phrase for ./demoCA/private/cakey.pem:
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 287 (0x11f)
Validity
Not Before: Jan 20 16:23:50 2006 GMT
Not After : Jan 20 16:23:50 2007 GMT
Subject:
countryName = CN
stateOrProvinceName = Beijing
organizationName = ZZNODE
organizationalUnitName = DI
commonName = huangbl
emailAddress = huangbili@263.net
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
95:F4:75:BE:3A:E0:DA:0C:76:49:0C:60:89:4F:64:58:AA:C7:18:F0
X509v3 Authority Key Identifier:
keyid:A6:4E:E1:7D:EC:BF:59:33:1D:16:30:3B:F3:4B:D4:C8:CC:B5:0E:75
Sign the certificate? [y/n]:y
Write out database with 1 new entries
Data Base Updated
Loading 'screen' into random state - done
Enter pass phrase for clikey.pem:
Enter Export Password:
Verifying - Enter Export Password:
已复制 1 个文件。