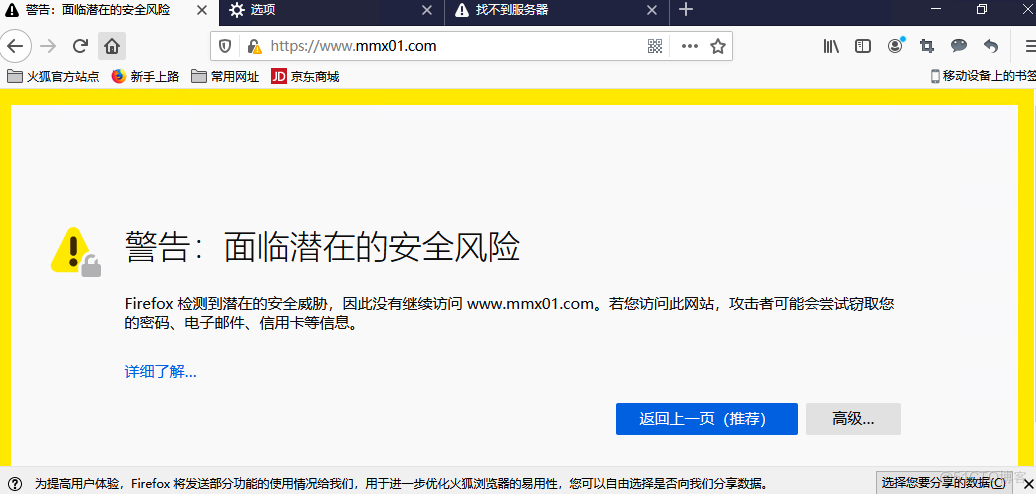
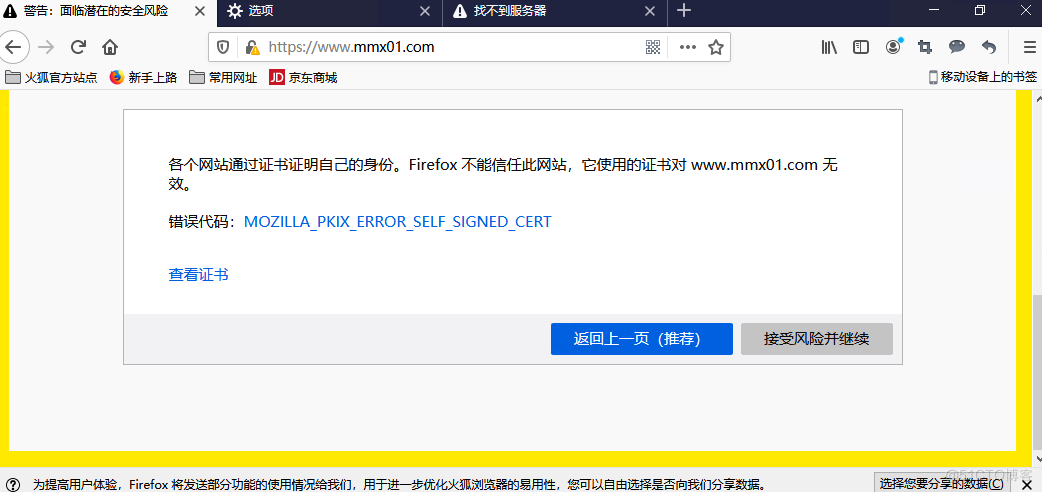
HTTPS,是以安全为目标的 HTTP 通道,在HTTP的基础上通过传输加密和身份认证保证了传输过程的安全性。
SSL可以用来加密web服务器和客户端之间的数据流,SSLv2存在一些问题,TLS随之而来,TLS传输层安全是在SSLv3之后定义的。在HTTPS的传输过程中,由CA(certificate authority)机构颁发证书,对私钥证书请求盖章,表示证书可信安全。
一、环境准备

操作系统 | 说明 | IP地址 |
centos | WEB服务器 | 172.16.10.1 |
win10 | 测试客户端 | 172.16.10.2 |
二、生成证书
证书文件 | 说明 |
key | 服务器私钥文件 |
csr | 证书请求文件 |
crt | CA签名证书(包含证书的相关信息) |
1、 安装mod_ssl软件
[root@web_server ~]# yum -y install httpd mod_ssl2、配置证书文件
2.1 key文件
[root@web_server ~/TLS]# openssl genrsa 2048 > server.key
Generating RSA private key, 2048 bit long modulus (2 primes)
..........................+++++
......+++++
e is 65537 (0x010001)
2.2 csr文件
[root@web_server ~/TLS]# openssl req -new -key server.key -out server.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:mmx
Organizational Unit Name (eg, section) []:mmx
Common Name (eg, your name or your server's hostname) []:www.mmx.com
Email Address []:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
2.3 crt文件
[root@web_server ~/TLS]# openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
Signature ok
subject=C = CN, ST = HB, L = WH, O = mmx, OU = mmx, CN = www.mmx.com
Getting Private key
3、查看证书文件
3.1 查看crt文件
[root@web_server ~/TLS]# openssl x509 -in server.crt -noout -text
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
03:3d:a6:ff:70:d1:e8:04:45:d6:0b:27:aa:c9:28:e5:fe:85:1a:df
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = HB, L = WH, O = mmx, OU = mmx, CN = www.mmx.com
Validity
Not Before: Feb 2 03:50:30 2023 GMT
Not After : Feb 2 03:50:30 2024 GMT
Subject: C = CN, ST = HB, L = WH, O = mmx, OU = mmx, CN = www.mmx.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:d1:cf:97:ab:30:7a:3c:20:47:a3:e3:c9:94:f9:
b7:93:6f:a6:7f:5e:20:b1:5b:d1:bc:1d:83:65:b4:
f9:eb:91:6f:e7:f6:b3:68:d8:0d:09:a2:e2:90:11:
0b:63:b0:a6:ef:4e:b2:14:d1:c5:29:36:d6:d0:8c:
78:6c:86:b4:0a:8e:ae:4a:f4:0a:02:13:04:c4:16:
47:2e:ad:bf:9a:f2:6a:20:d0:05:6b:89:73:bb:91:
63:73:e6:59:3a:fe:f8:80:f0:06:77:06:5b:3c:bb:
b9:7b:b7:66:6e:8e:b0:33:31:fa:3e:f5:ff:bf:a4:
2a:e2:e0:3d:9f:30:5b:4d:9c:78:b4:c4:98:45:f5:
bd:d5:4b:a0:bc:5e:43:59:06:84:25:50:50:56:df:
f3:39:ee:62:b8:43:30:e2:c5:96:d0:19:12:37:1e:
f8:c9:5d:1d:21:16:71:c0:1d:5f:69:91:12:9e:e4:
ec:b6:a2:5f:c2:86:09:ca:5f:c0:2b:05:e5:16:c2:
ee:f5:94:d5:54:43:28:24:4d:fb:55:3b:76:59:b8:
01:28:a6:69:03:94:86:d9:a3:b9:e7:a2:1a:4d:5e:
2c:73:3b:db:0b:48:e2:32:ee:36:66:3e:60:f5:b5:
af:97:4d:2b:91:fc:4f:20:61:84:99:3e:23:06:14:
79:17
Exponent: 65537 (0x10001)
Signature Algorithm: sha256WithRSAEncryption
d0:54:7e:7b:0b:7e:7f:33:c9:d7:37:b7:2c:08:3a:9f:7c:9b:
e1:e9:c0:4c:d7:fb:c0:e0:00:1a:89:0b:7e:2a:0f:d0:f6:57:
83:04:1d:ac:a6:3a:e9:c9:60:d3:e6:bc:a9:ff:31:37:4d:82:
e1:41:7e:17:12:06:7a:47:74:a1:37:f7:ed:98:3f:04:51:68:
51:c7:4a:d6:cb:49:1c:2e:5f:40:fd:9a:90:99:32:e1:92:a1:
f5:47:54:2e:7c:63:f7:13:6f:ac:3c:a7:81:e9:20:64:29:6f:
1e:99:ac:d9:aa:17:91:ce:03:c7:ec:c9:6c:0f:d2:db:cd:98:
8c:3c:01:8f:9e:55:39:99:c2:e8:02:8e:4f:7e:6a:00:84:0f:
8e:a8:15:92:ca:41:20:ef:24:ee:0b:7f:e6:66:97:51:de:5d:
c1:47:ee:8e:2c:1f:c5:b0:aa:f9:a9:93:e0:ed:3c:76:e2:19:
b3:7a:9e:35:6c:a6:38:9f:70:36:ba:bb:ad:27:27:5f:41:2e:
20:63:43:fd:2b:15:30:26:86:3a:a8:78:5d:08:50:ba:d3:aa:
94:d7:dc:cf:32:62:a0:19:b2:9a:ab:14:59:ed:d0:dc:fe:0e:
86:c8:b3:11:5d:cc:ee:6a:6c:5c:bc:00:7e:c1:82:6d:55:ca:
b1:f0:d6:d0
3.2 查看csr文件
[root@web_server ~/TLS]# openssl req -in server.csr -noout -text
Certificate Request:
Data:
Version: 1 (0x0)
Subject: C = CN, ST = HB, L = WH, O = mmx, OU = mmx, CN = www.mmx.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:d1:cf:97:ab:30:7a:3c:20:47:a3:e3:c9:94:f9:
b7:93:6f:a6:7f:5e:20:b1:5b:d1:bc:1d:83:65:b4:
f9:eb:91:6f:e7:f6:b3:68:d8:0d:09:a2:e2:90:11:
0b:63:b0:a6:ef:4e:b2:14:d1:c5:29:36:d6:d0:8c:
78:6c:86:b4:0a:8e:ae:4a:f4:0a:02:13:04:c4:16:
47:2e:ad:bf:9a:f2:6a:20:d0:05:6b:89:73:bb:91:
63:73:e6:59:3a:fe:f8:80:f0:06:77:06:5b:3c:bb:
b9:7b:b7:66:6e:8e:b0:33:31:fa:3e:f5:ff:bf:a4:
2a:e2:e0:3d:9f:30:5b:4d:9c:78:b4:c4:98:45:f5:
bd:d5:4b:a0:bc:5e:43:59:06:84:25:50:50:56:df:
f3:39:ee:62:b8:43:30:e2:c5:96:d0:19:12:37:1e:
f8:c9:5d:1d:21:16:71:c0:1d:5f:69:91:12:9e:e4:
ec:b6:a2:5f:c2:86:09:ca:5f:c0:2b:05:e5:16:c2:
ee:f5:94:d5:54:43:28:24:4d:fb:55:3b:76:59:b8:
01:28:a6:69:03:94:86:d9:a3:b9:e7:a2:1a:4d:5e:
2c:73:3b:db:0b:48:e2:32:ee:36:66:3e:60:f5:b5:
af:97:4d:2b:91:fc:4f:20:61:84:99:3e:23:06:14:
79:17
Exponent: 65537 (0x10001)
Attributes:
a0:00
Signature Algorithm: sha256WithRSAEncryption
a3:11:08:2a:f6:a8:25:67:26:bf:52:dd:18:f8:45:15:cb:77:
ad:f1:79:0e:15:8a:4c:08:48:58:26:57:b3:81:6d:d0:80:57:
bd:8e:51:94:8e:f5:c7:37:0d:ff:00:bd:92:51:4f:24:93:39:
86:05:77:5b:44:f7:c4:03:3a:36:55:7a:10:7c:70:44:84:4e:
29:cc:a5:70:f5:6b:2e:dd:ef:74:70:ac:58:e2:14:58:54:b4:
fc:a1:c8:60:ba:ab:19:28:4b:d8:7a:94:a7:7c:2e:8c:3c:8d:
bd:6d:62:df:c0:17:b4:86:7a:8d:b0:cc:d1:f0:3e:99:46:10:
ec:18:c2:cc:a0:f7:5e:75:ae:5a:ed:0c:bf:dc:70:56:51:a8:
9e:23:a4:a9:16:2c:1a:e8:c8:13:f8:72:17:9f:9e:dd:b2:5a:
5e:a3:31:33:cd:1e:ff:af:2f:21:63:6c:34:dc:ed:78:f3:e0:
97:a1:09:21:77:f2:5a:94:6b:60:83:c1:ad:cb:ff:81:62:b0:
e1:b5:25:a6:96:9f:4f:70:f6:f7:b0:47:90:65:ed:76:49:c1:
10:4e:25:e4:5a:06:7b:77:4c:5e:4c:b8:fa:b5:8f:12:db:7e:
a5:30:3f:9e:78:77:71:5a:6d:28:18:91:22:72:13:fd:f6:ea:
13:0f:d0:8e
4、 将文件移入http配置文件
[root@web_server ~]# mv TLS/server.* /etc/httpd/conf.d/二、 配置HTTPS
1、 编辑配置文件
默认ssl文件:/etc/httpd/conf.d/ssl.conf
[root@web_server /etc/httpd/conf.d]# cat ssl.conf
Listen 443 https
<VirtualHost _default_:443>
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLEngine on
SSLHonorCipherOrder on
SSLCertificateFile /etc/httpd/conf.d/server.crt
SSLCertificateKeyFile /etc/httpd/conf.d/server.key
CustomLog logs/ssl_request_log \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
2、虚拟主机配置
[root@web_server /etc/httpd/conf.d]# cat /etc/httpd/conf.d/site1.conf
<VirtualHost 172.16.10.1:80>
ServerName www.mmx01.com
Redirect "/" "https://www.mmx01.com"
<Directory /home/mmx/site/www/site1/>
Require all granted
</Directory>
</Virtualhost>
<VirtualHost 172.16.10.1:443>
# ssl配置文件
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLEngine on
SSLCertificateFile /etc/httpd/conf.d/server.crt
SSLCertificateKeyFile /etc/httpd/conf.d/server.key
ServerName www.mmx01.com
DocumentRoot /home/mmx/site/www/site1/
<Directory /home/mmx/site/www/site1/>
Require all granted
</Directory>
</Virtualhost>
3、 编辑index.html文件
[root@web_server ~]# mkdir /home/mmx/site/www/site1/
[root@web_server ~]# echo "this is site1 " > /home/mmx/site/www/site1/index.html
# 设置临时selinux
[root@web_server ~]# chcon -t httpd_sys_content_t /home/mmx/site/www/site1/
[root@web_server ~]# chcon -t httpd_sys_content_t /home/mmx/site/www/site1/*
4、 放行防火墙
[root@web_server ~]# firewall-cmd --add-service=https --permanent
[root@web_server ~]# firewall-cmd --add-service=http --permanent
[root@web_server ~]# firewall-cmd --reload
5、 ansible生成证书
可以使用ansible自动生成证书文件
---
- name: 生成证书
hosts: XXX
tasks:
- name: 创建文件夹
file:
path: /etc/pki/tls/private/
state: directory
recurse: yes
- name: 安装openssl
yum:
name: openssl
state: present
- name: 安装python3-pyOpenSSL
yum:
name: python3-pyOpenSSL
state: present
- name: 创建RSA私钥
openssl_privatekey:
path: /etc/pki/tls/private/mmx.rsa.key
- name: 确保密钥生成
openssl_privatekey:
path: /etc/pki/tls/private/mmx.ecdsa.key
type: ECC
curve: secp256r1
- name: 生成CSR文件
openssl_csr:
path: /etc/pki/tls/private/mmx.csr
privatekey_path: /etc/pki/tls/private/mmx.rsa.key
subject_alt_name: "DNS:demo.example.com,DNS:www.example.com"
common_name: demo.example.com
C: CN
ST: hubei
L: wuhan
O: mmx
backup: yes
- name: 生成CRT文件
community.crypto.x509_certificate:
path: /etc/pki/tls/certs/mmx.crt
privatekey_path: /etc/pki/tls/private/mmx.rsa.key
csr_path: /etc/pki/tls/certs/mmx.csr
provider: selfsigned
三、测试
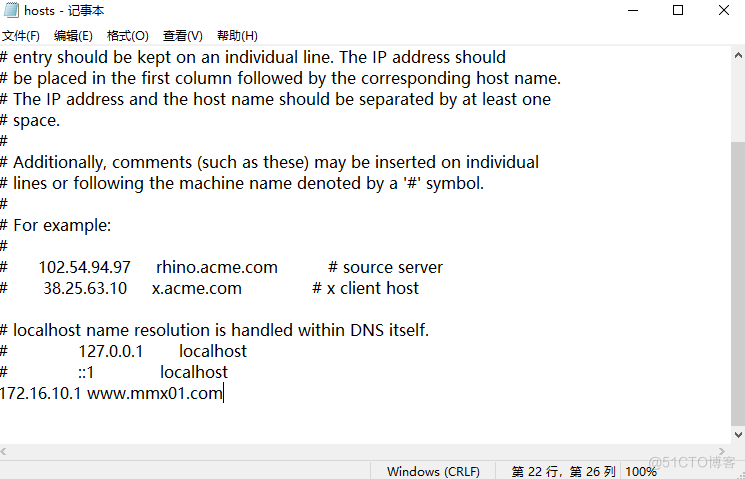
1、 编辑hosts文件
C:\Windows\System32\drivers\etc\hosts
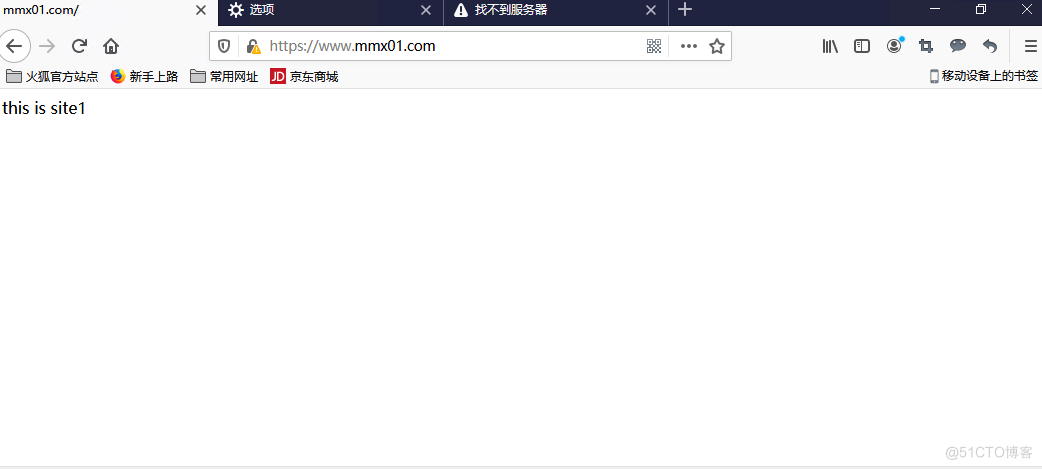
2、浏览器输入ip地址访问web服务器
3、成功访问