文章目录
MISC
签到
赛博德国人
MISC520
Baby_Forenisc
Crypto
Bigrsa
Ring Ring Ring
MISC
签到
题目描述:猜数字01-30,数字序列以Sanfor{md5(**-**-**-**)}形式提交
附件为一张gif
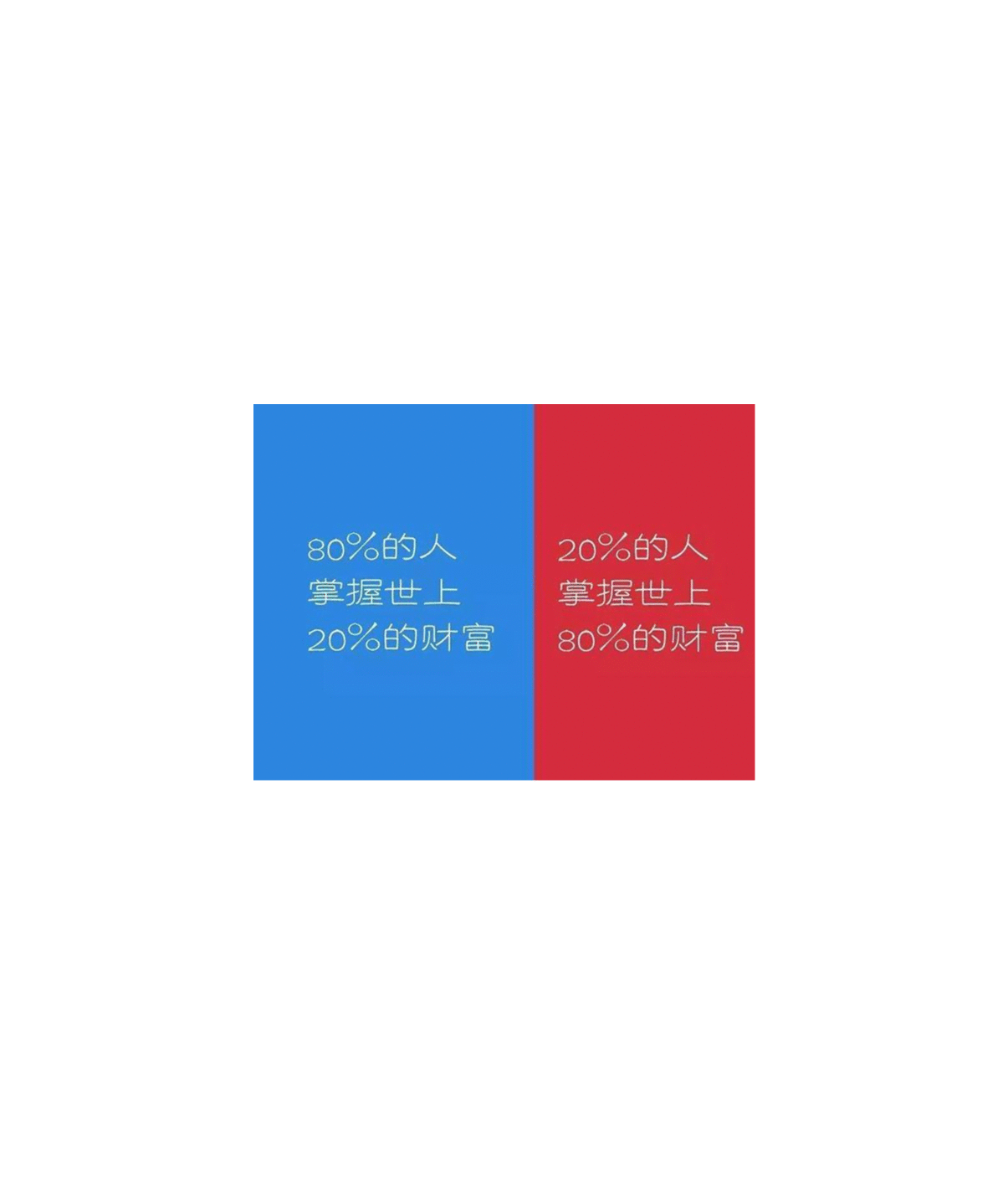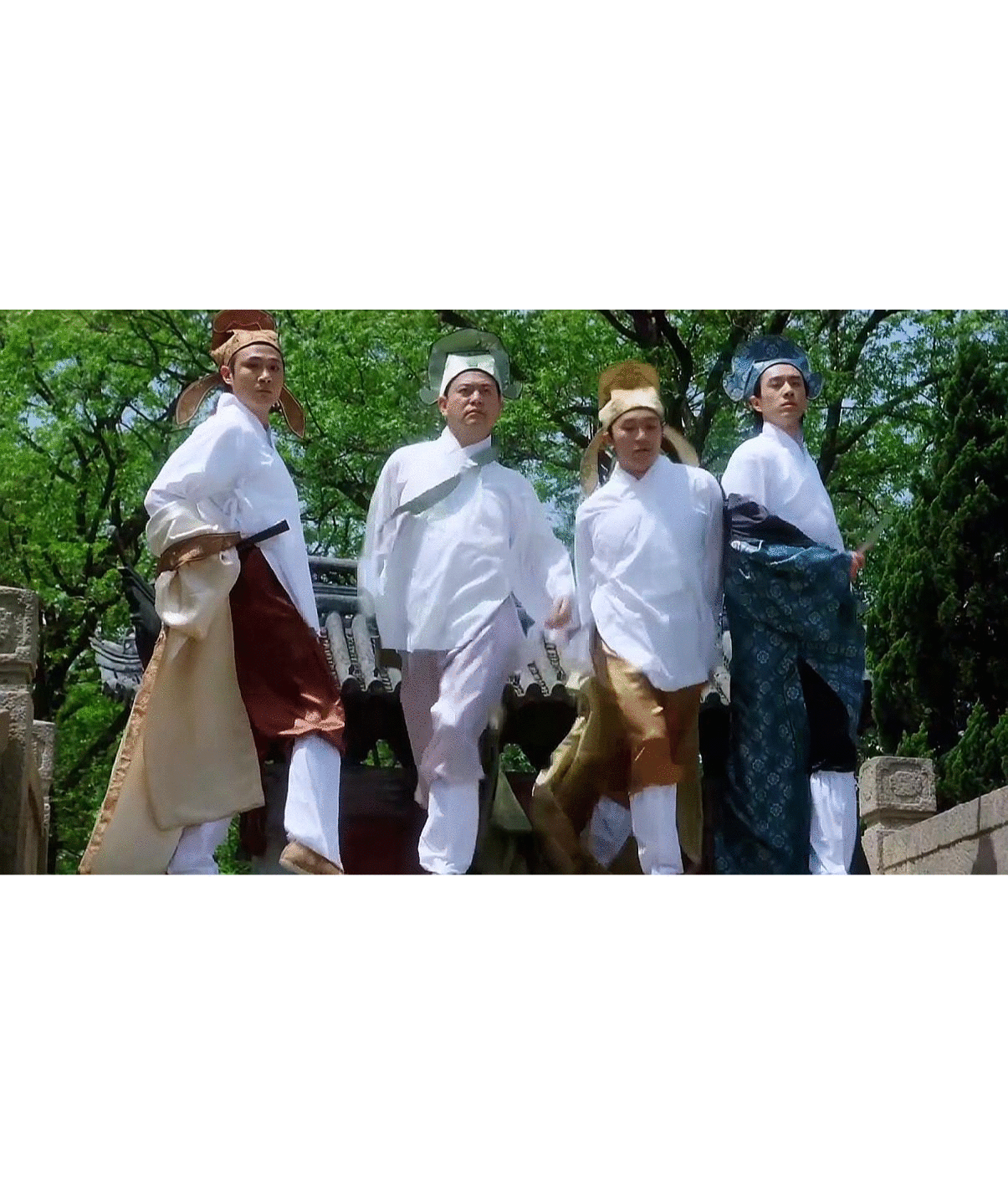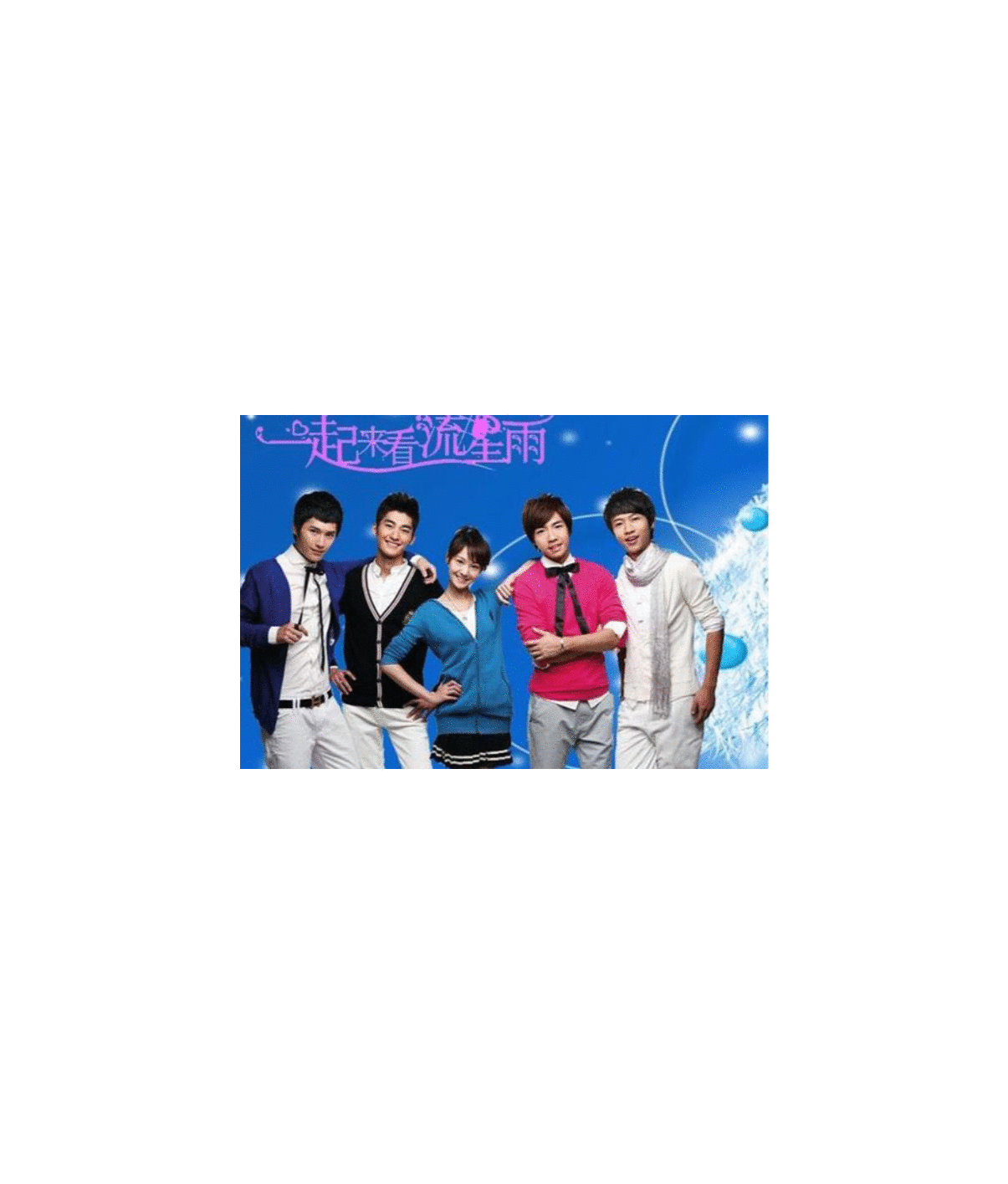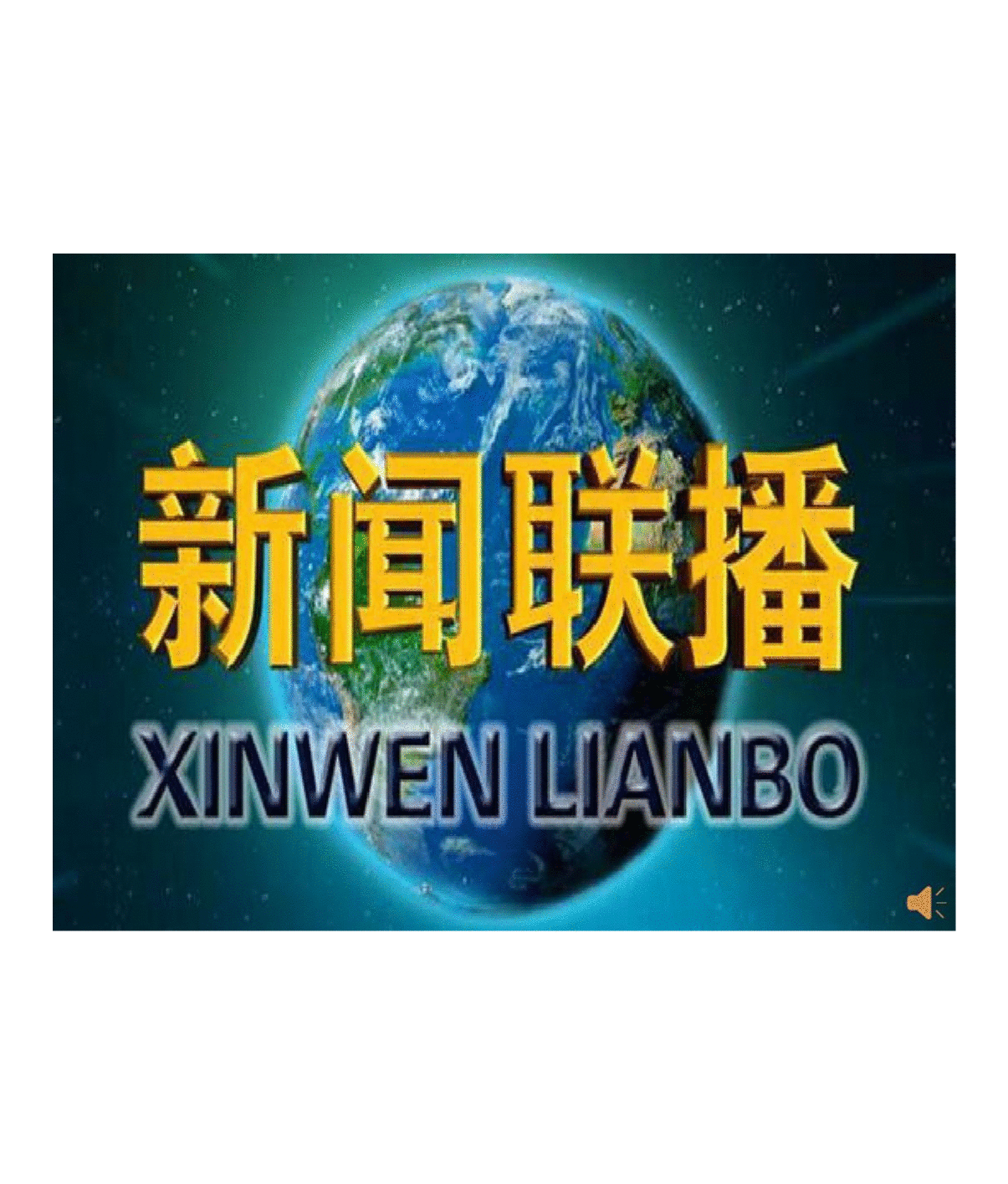
猛猜
图1 28准则
图2 8卦阵
图3 30而立之年
图4 北斗7星
图5 4大才子
图6 歼-20
图7 2只黄鹂鸣翠柳
图8 17来看流星雨
图9 23号乔丹
图10 1马当先
图11 12黄道
图12 新闻联播每晚19点首播
得到序列
md5(28-08-30-07-04-20-02-17-23-01-12-19)
#SangFor{d93b7da38d89c19f481e710ef1b3558b}赛博德国人
winrar打开题目附件,惊喜发现hint

解压之后为一个CyberGerman.pcapng流量包,打开之后发现里面有两文件

分别追踪TCP数据流导出

拿到一个codebook.pdf以及encrypyed.txt
尝试打开codebook.pdf,居然还是加密的

回去找密文,在流量包里发现疑似密文的数据

codebook.pdf输入密码后果然对了,打开发现像是一个密码表。

codebook.pdf
查看encrypyed.txt
0911 = 1tle = 1tl = 350(长度) = RZS NAJ(PKS) =
nkfgp roqad boprv yrdhy zwamf qsrhb owqvt jzotr ffcjq snpqh kpwzm fprru gufez xsuws aohyw xbreu pifbz kagxj blbha jzixj zrasn zxkay lpaza ejwou itcip dfdgp rbjnv xuqzq qhtya xwwik wyybx kdgrc slrkj pgjay aidwa jeszp pbqat njojg jrplb kkhot joqpg vwecj soabm aupsr fenug ybxmr jloch kmjgc tznxl tnrqx pbeph fwymn gpoor pjkkb plkwb kxzeq quorp ipuvs utyae qyzgp mqnai iysse gzsht tsrmv crrkr opuxj tqshv ypdrw rvnzt cstlj又是一堆看不懂的东西,这时候就要上百度谷歌了,查阅资料
得知加密为恩尼格玛密码机。
在密码学史中,恩尼格玛密码机(德语:Enigma,又译哑谜机,或“谜”式密码机)是一种用于加密与解密文件的密码机。确切地说,恩尼格玛是对二战时期纳粹德国使用的一系列相似的转子机械加解密机器的统称,它包括了许多不同的型号,为密码学对称加密算法的流加密。
开始破译
#encrypted.txt
0911 = 1tle = 1tl = 350 = RZS NAJ=
nkfgp roqad boprv yrdhy zwamf qsrhb owqvt jzotr ffcjq snpqh kpwzm fprru gufez xsuws aohyw xbreu pifbz kagxj blbha jzixj zrasn zxkay lpaza ejwou itcip dfdgp rbjnv xuqzq qhtya xwwik wyybx kdgrc slrkj pgjay aidwa jeszp pbqat njojg jrplb kkhot joqpg vwecj soabm aupsr fenug ybxmr jloch kmjgc tznxl tnrqx pbeph fwymn gpoor pjkkb plkwb kxzeq quorp ipuvs utyae qyzgp mqnai iysse gzsht tsrmv crrkr opuxj tqshv ypdrw rvnzt cstlj
对于encrypted.txt结构分析
0911 猜测为接受到信息的日期
1tle 为发送方姓名
1tl 为接收方姓名
350 为密文长度为350位
RZS NAJ 为加密转子起始位置解密信号
首先确认信息发送的日期
密码段的前五位为标志位,通常为设定的三个字母加上任意的两个字母组成
前五个数据为nkfgp,去codebook.pdf中寻找
|Tag | Walzenlage |Ringstellung| Steckerverbindungen | Kenngruppen |
| 10 | II III I | 05 21 25 | AT BV CF EN GY HO IW LU MZ QX | SUW FGP OGA CRB |
确认到10号的Kenngruppen一栏中含有FGP,锁定信息发送的日期,开始破译。祭出模拟软件。

Enigma模拟软件
继续破译
|Tag | Walzenlage |Ringstellung| Steckerverbindungen | Kenngruppen |
| 10 | II III I | 05 21 25 | AT BV CF EN GY HO IW LU MZ QX | SUW FGP OGA CRB |
调整密码机模式Kriegsmarine M3 - UKW = C(我也不知道为什么,乱试出来的)
选取转子序号II III I
将三个转子分别调整到05 21 25对应'E' 'U' 'Y'
随后按照Steckerverbindungen对字母进行连线

内部转子设置
按照Steckerverbindungen对字母进行连线

按照Steckerverbindungen设置
根据encrypted.txt的第一行信息 = RZS NAJ =确认破译转子起始位置,确认方法:配置好设备后将表面三个转盘调整至RZS,随后往密码机中键入NAJ(直接点模拟机中的键盘也可),密码机输出PKS,其中PKS代表译文转子起始位置。

随后将表面三个转盘调整至PKS就可以开始快乐打印了,记得把前五个标志位nkfgp去除
#打印得到信息
VIERSIEBENFUENFSIEBENVIERACHTFUENFVIERSIEBENBERTADREISECHSSECHSZWEIDREINEUNDREISECHSDREISIEBENDREIZWEIDREINULLDREIFUENFSECHSSECHSSECHSFUENFDREISIEBENDREIFUENFDREISIEBENDREINEUNDREIFUENFSECHSSECHSDREIEINSDREINULLDREIVIERDREIACHTDREIFUENFDREISIEBENDREIEINSSECHSDREISECHSSECHSDREIVIERSECHSDREISECHSSECHSSECHSZWEIDREISIEBENDREINULLDREIDREISIEBENDORA猜测为德语,直接百度德语数字

使用Notepad++文本替换
475748547BERTA36623936373230356665373537393566313034383537316366346366623730337DORA其中BERTA为b,DORA为d,显而易见16进制转文本

MISC520
题目描述:有一天,zip爱上了pcap,zip为了能与pcap创造更多机会,不断地将自己的能力表现出来。可是,LSBSteg却突然杀了出来,将pcap吞并于png中,不放出来
。zip看到了png,多喝热水少做梦。zip异常的愤怒,不断地用自己的能力去报复png,不让png逃走。至今,zip仍未释怀。
好家伙,一看就是套娃题,什么zip、pcap、lsb、png...一个个来
首先给了一个压缩包520.zip,解压后得到519.zip和story,story打开和题目描述一样,519.zip解压后是518.zip和一样的story(套娃)。

写脚本解压
import zipfile
# 解压文件夹
file_input = 'D:/2021.9羊城杯/misc520-2fee7e6e-92ea-46f9-b382-e8ca5e7534ba/1/'
# 解压目标文件夹
file_output = 'D:/2021.9羊城杯/misc520-2fee7e6e-92ea-46f9-b382-e8ca5e7534ba/1/'
def zip_file(zip_name):
# print(zip_name)
r = zipfile.is_zipfile(zip_name)
if r:
fz = zipfile.ZipFile(zip_name, 'r')
for file in fz.namelist():
fz.extract(file, file_output)
for i in range(519, 0, -1):
zip_file(file_input + "{}.zip".format(i))
story = open(file_input + "story", 'r', encoding='UTF-8').read()
if 'png' in story:
pass
else:
print(story)
#print
"""
这都被你发现了?
我这故事不错吧,嘻嘻嘻
那就把flag给你吧
oh,不,还有一半藏在了pcap的心里,快去找找吧
左心房右心房,扑通扑通的心,咿呀咿呀的❤
72, 89, 75, 88, 128, 93, 58, 116, 76, 121, 120, 63, 108,
"""拿到一串数字,提示去找另一串,解压完所有文件后拿到张图flag.png,打开Stegsolve
flag.png
0通道有东西

Data Extract尝试后找到PK头

导出压缩包数据,发现是个加密的压缩包,里面有flag.pcap,没找到密码尝试弱密码爆破。


打开flag.pcap,认定为USB流量隐写,Leftover Capture Data为4字节,锁定鼠标流量。

flag.pcap
使用tshark命令把该流量分析包输出为一个名为usbdata的文本
tshark -r flag.pcap -T fields -e usb.capdata > usbdata.txt祭脚本
#将数据0005fa00转化为00:05:fa:00四字节格式
#第一字节为00代表鼠标按键未按下,01代表鼠标左键按下,02代表鼠标右键按下
#第二字节为鼠标水平移动距离
#第三字节为鼠标垂直移动距离
while 1:
a=f.readline().strip()
if 1:
if len(a)==8: # 鼠标流量的话len改为8
out=''
for i in range(0,len(a),2):
if i+2 != len(a):
out+=a[i]+a[i+1]+":"
else:
out+=a[i]+a[i+1]
fi.write(out)
fi.write('\n')
else:
break
fi.close()将16进制的usbdata.txt转为坐标
nums = []
keys = open('usbdata.txt','r')
f = open('xy.txt','w')
posx = 0
posy = 0
for line in keys:
if len(line) != 12 :
continue
x = int(line[3:5],16)
y = int(line[6:8],16)
if x > 127 :
x -= 256
if y > 127 :
y -= 256
posx += x
posy += y
btn_flag = int(line[0:2],16) # 1 for left , 2 for right , 0 for nothing
if btn_flag != 0 : # 输出鼠标有按键按下后的坐标
f.write(str(posx))
f.write(' ')
f.write(str(posy))
f.write('\n')
f.close()上gnuplot,把xy.txt文本里的坐标转化为图片
gnuplot.exe plot "xy.txt"
最后拿到数字串
72, 89, 75, 88, 128, 93, 58, 116, 76, 121, 120, 63, 108, 130, 63, 111, 94, 51, 134, 119, 146好了,开始和出题人对脑电波,题目flag格式GWHT{},对比猜测为ASCII码加密,每位减去相应位数。如72为第一位chr(72-1)='G',89为第二位chr(89-2)='W'等等。
a = [72, 89, 75, 88, 128, 93, 58, 116, 76, 121, 120, 63, 108, 130, 63, 111, 94, 51, 134, 119, 146]
flag = ''
for i in range(len(a)):
flag = flag + chr(a[i] - i - 1)
print(flag)
#GWHT{W3lCom3_t0_M!sc}Baby_Forenisc
内存取证题目,题目给了一个raw文件,上kali打开volatility常规检测。
python vol.py -f 1.raw --profile=WinXPSP2x86 cmdscan
Volatility Foundation Volatility Framework 2.6.1
CommandProcess: csrss.exe Pid: 580
CommandHistory: 0x566bb8 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 5 LastAdded: 4 LastDisplayed: 4
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x4cc
Cmd #0 @ 0x3689ed8: git push -u origin master
Cmd #1 @ 0x566148: ok....
Cmd #2 @ 0x56aa08: then delete .git and flagfile
Cmd #3 @ 0x368a798: You can never find my account
Cmd #4 @ 0x56a580: hahaha!提示东西在git上,找找能不能找到涉及到git具体仓库的信息。
python vol.py -f 1.raw --profile=WinXPSP2x86 filescan|grep "txt"
Volatility Foundation Volatility Framework 2.6.1
0x00000000020bf6a0 1 0 RW-r-- \Device\HarddiskVolume1\Documents and Settings\Owner\桌面\ssh.txt
0x00000000021c01b0 1 0 R--rwd \Device\HarddiskVolume1\Documents and Settings\All Users\ssh.txt
0x000000000231d6b0 4 2 -W-rw- \Device\HarddiskVolume1\Documents and Settings\All Users\Application Data\VMware\VMware VGAuth\logfile.txt.0找ssh.txt文件,dump出来改文件后缀为txt。
python vol.py -f 1.raw --profile=WinXPSP2x86 dumpfiles -Q 0x00000000020bf6a0 -D ./#ssh.txt
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAmw8eqi/h23ABuRhhmx83LuRhw6m8C8k76Me0s7MNdvDP2ZB5hJUU
fZ4HxR5sEoQf6NyIcCDeznb8FAYAktm3cBlgof847aL661F0R5FtIfOJC/MwklRmXjYr46
6HNjQ0Ouu12znqBPJAaMkAaZXknqlEAxCRvyOQhg0bPSR3xxCM39TxpXRKd3tzhlBUQHZi
upgt6CF3TkBuIcKUPgZ7OgJ/7ES3FaiUOlpZdUYf/H3VwwQumuXPPwvT5QdRA9Myv/zbee
R9ddLJL84raHK6unuHjngGvWjhXUUQulta49HH55pyrFUViIvH1tfns/6BglTrYWRlFX3A
TNOVy2igHkhZI8M9GK5VUBwEo3kXcWRiK85vAWwmddBd9+c0NERahRg+SNbodsd1JFu0C9
kqJ8/HlOnDfPBsUpD0EY/EbzW5PKbkksp2Vp3z+S0y1aVpX2EJRhq2S5kEEU+V4LLN6uqu
CJzVLeG5Lpnn4V/Ekf/ZpJmmk1Pp9KGFw3tlOqTLAAAFkNMuPgLTLj4CAAAAB3NzaC1yc2
EAAAGBAJsPHqov4dtwAbkYYZsfNy7kYcOpvAvJO+jHtLOzDXbwz9mQeYSVFH2eB8UebBKE
H+jciHAg3s52/BQGAJLZt3AZYKH/OO2i+utRdEeRbSHziQvzMJJUZl42K+OuhzY0NDrrtd
s56gTyQGjJAGmV5J6pRAMQkb8jkIYNGz0kd8cQjN/U8aV0Snd7c4ZQVEB2YrqYLeghd05A
biHClD4GezoCf+xEtxWolDpaWXVGH/x91cMELprlzz8L0+UHUQPTMr/823nkfXXSyS/OK2
hyurp7h454Br1o4V1FELpbWuPRx+eacqxVFYiLx9bX57P+gYJU62FkZRV9wEzTlctooB5I
WSPDPRiuVVAcBKN5F3FkYivObwFsJnXQXffnNDREWoUYPkjW6HbHdSRbtAvZKifPx5Tpw3
zwbFKQ9BGPxG81uTym5JLKdlad8/ktMtWlaV9hCUYatkuZBBFPleCyzerqrgic1S3huS6Z
5+FfxJH/2aSZppNT6fShhcN7ZTqkywAAAAMBAAEAAAGAdfojEsorxpKKPRLX8PbnPb52xD
C46x7Jfmu0iaWKcRz4iEjsrHvhg1JiBxEGmW/992cUSHw6Ck1trq6CcTlF4PzuEVPnNKf0
0ma/WlTD/DkX5Qe7xRqCaNw+uJVqO0utEceWLp7595l6eD+3GJ77u9x96vcIba3ZoKUIPJ
UqrUNibEvRMFoy7oX3eBJWiFWK+P4gr6YG6HsNUJKDyE2WJKUSP+pogwoo/d0Qg7I/VBVK
N39PFnwUG5wcNP5EHezqWQVVln/dltDgOc5IldknTRt4Q3NDrSyNsRpv0EYI2gz+yRu/IE
RR9PHYjH5l6uYwowW34iGi/xloSxG5bDEWOe0eEANCjowiYYrmTLffIQ/AU9w4te/+eWd2
WV56LUuC6k4mEdNhtljMZR/0A+C5EkPzgsTEJEmYLYvqrNejM7Y1UKz3+YZ8m8rT4XcNmf
j5wfJd1TbCu0hB5kZC1DkybYQaMRNnZ3+PjwU2hZBTuh02F787nG5NFkpI96qkWxTBAAAA
wBdaxLNzl/7Dig/neTUAQLa/C1F2cpQt6RcJbzHodgxm8n75a/wdRI4/oCvGJkRgyAnyCE
tgfMnTQ4opmHf5k0U0R/wmCGivcGhg5KIBSSnp9mWt6qclJ8O6vZ5L3rKIgreWzGUDk8IT
W3Lcl5EO0sskpVvp65xncEdv3CefxXVTlkgp4PXgXcxPao633hWA6TAm2zZx7R6fJt0Ex4
x3lVG68ghRE/ZFbF48s8Gy+zRDyA5JEGPWxWddO623IVgG6AAAAMEAyX4CJKSxE5gvJdrw
lhx8dBbVQxw06fPoVlu/z/JTwkPdliuAdp30SV8WbmXUhLvv457WdqAMCwlGs/7xrCW21U
84+VeD9aGM61nSsT7kUzGjdvbjQiHCmys7dwuy/thCrpWFTxI4fjOEYHc3N8S+hBHQRJKk
mEYyBoI3eJ3NhUsGHr1V4LONBKkoUZyC+LjKev06m9qM6R0/0k4cB09pkDVinuFuGk5iDy
YKyjAGiAxFI9ACiZ5NLKTsdaEqtCPfAAAAwQDFAXbSxwbLYWDacBNUm4E7FZsYKkqoIAWQ
3uEQP5Sp7GrCU5dWraGB2wOkX+irMYGDfTk5qG8NLyYoSKVIZwA6ijDliWekL6XdPGJfKK
7xw64Nx6syc7oD7scSzTGNH0m1z+T2rjP3dMDDVhYMHksYcSxikyHNzLR9Z51hCOHeKb1O
8LNW4IrC6AYeXt8sHizSLIagncOuPtSkKiGdR5fn65fHomMzaVQsSJYvwNeSrKXu36NSJm
27AuL6DDE2vJUAAAAUc29uZzU1MjA4NTEwN0BxcS5jb20BAgMEBQYHbase64解密,看到最后包含一个邮箱song552085107@qq.com,接下来直接上Github。
openssh-key-v1nonenone�ssh-rsa���/��p�a�7.�aé��;�Ǵ��
v��ِy��}��l��܈p ��v��ٷp`��8����QtG�m!��0�Tf^6+㮇644:��9��@h�i�䞩D��#��
=$w�����tJw{s�PT@vb��-�!wN@n!>{:�D���:ZYuF�}��.���?��Q�2���y�}u��/�+hr��{��x�h�]E�[Z����r�U���������T�ade}�Lӕ�h�HY#�=�UP�yqdb+�ol&u�]��44DZ�>H��v�u$[��*'�ǔ��|�lR����o5�<���vV���-2եi_a F�K�O�������-�.���_đ�٤���S�����{e:����.>�.>ssh-rsa���/��p�a�7.�aé��;�Ǵ��
v��ِy��}��l��܈p ��v��ٷp`��8����QtG�m!��0�Tf^6+㮇644:��9��@h�i�䞩D��#��
=$w�����tJw{s�PT@vb��-�!wN@n!>{:�D���:ZYuF�}��.���?��Q�2���y�}u��/�+hr��{��x�h�]E�[Z����r�U���������T�ade}�Lӕ�h�HY#�=�UP�yqdb+�ol&u�]��44DZ�>H��v�u$[��*'�ǔ��|�lR����o5�<���vV���-2եi_a F�K�O�������-�.���_đ�٤���S�����{e:���u�#�+ƒ�=����=�v�0���~k����q��H�{�Rb�o��gH|:
Mm���q9E���S�4���f�ZT��9����h�>��j;K�ǖ.����zx?�����}��m�٠�<�*�CblK�0Z2��xV�U��� ���{
P���M�$�?�h�
(����?TJ7O|�4�D��YU�ݖ��9�H��'MxCsC�,��o�F���� DQ��،~e��0���!��hK�l19�B��"a��L��!�S�8���ygvY^z-K��N&�a�X�e��C���$I�-��ף3�5P����|����w
�����]�6»HA�FB�92m�1gg��6��S�6�;�nMJH���[��Zijs��Ê�y5@��Qvr�-� o1�vf�~�k�D�?�+�&D`� �K`|��C�)�w��E4G�&h�ph`�I)��e��%'ú��K�����e��[rܗ���$�[��gpGo�'��uS�H)���]�Oj�����0&�6q��&�njw�Q��Q�El^<����4C�Ic��g];��!X���~$���/%��|t�C4���V[���S�Cݖ+�v��I_neԄ����v� F���%��O8�W�����Yұ>�S1�v��B!+;w���B���O8~3�`w77ľ��D���F2�7x�ͅK�U್�(Q�����z�:�ڌ�?�NOi�5b��nNb&
�0�E#���M,��u�*�#���v���a`�pT��;�*J� ���?���j�S�V�����_�1��}99�o
/&(H�Hg:�0�g�/��<b_(��î
ǫ2s����1�I�����3�t��VKq,b�!�̴}g�a��)�N�V����^�,,�,���î>Ԥ*!�G���Ǣc3iT,H�/�ג���ߣR&m���16��song552085107@qq.com

Notepad++打开_APP_,开始翻文件找找找,找到熟悉的。

继续Base64解密
U2FuZ0ZvcntTMF8zYXp5XzJfY3JhY2tfbm9vYl9wbGF5ZXJ9
#base64:SangFor{S0_3azy_2_crack_noob_player}Crypto
Bigrsa
题目:
from Crypto.Util.number import *
from flag import *
n1 = 103835296409081751860770535514746586815395898427260334325680313648369132661057840680823295512236948953370895568419721331170834557812541468309298819497267746892814583806423027167382825479157951365823085639078738847647634406841331307035593810712914545347201619004253602692127370265833092082543067153606828049061
n2 = 115383198584677147487556014336448310721853841168758012445634182814180314480501828927160071015197089456042472185850893847370481817325868824076245290735749717384769661698895000176441497242371873981353689607711146852891551491168528799814311992471449640014501858763495472267168224015665906627382490565507927272073
e = 65537
m = bytes_to_long(flag)
c = pow(m, e, n1)
c = pow(c, e, n2)
print("c = %d" % c)
# output
# c = 60406168302768860804211220055708551816238816061772464557956985699400782163597251861675967909246187833328847989530950308053492202064477410641014045601986036822451416365957817685047102703301347664879870026582087365822433436251615243854347490600004857861059245403674349457345319269266645006969222744554974358264尝试发现n1与n2存在公因数,分别计算分解出各自pq,常规RSA解密。
import binascii
import gmpy2
n1 = 103835296409081751860770535514746586815395898427260334325680313648369132661057840680823295512236948953370895568419721331170834557812541468309298819497267746892814583806423027167382825479157951365823085639078738847647634406841331307035593810712914545347201619004253602692127370265833092082543067153606828049061
n2 = 115383198584677147487556014336448310721853841168758012445634182814180314480501828927160071015197089456042472185850893847370481817325868824076245290735749717384769661698895000176441497242371873981353689607711146852891551491168528799814311992471449640014501858763495472267168224015665906627382490565507927272073
e = 65537
c = 60406168302768860804211220055708551816238816061772464557956985699400782163597251861675967909246187833328847989530950308053492202064477410641014045601986036822451416365957817685047102703301347664879870026582087365822433436251615243854347490600004857861059245403674349457345319269266645006969222744554974358264
p = gmpy2.gcd(n1, n2)
q1 = n1 // p
q2 = n2 // p
phi1 = (p - 1) * (q1 - 1)
phi2 = (p - 1) * (q2 - 1)
d1 = gmpy2.invert(e, phi1)
d2 = gmpy2.invert(e, phi2)
m = pow(pow(c, d2, n2), d1, n1)
print(binascii.unhexlify(hex(m)[2:].strip("L")))
#SangFor{qSccmm1WrgvIg2Uq_cZhmqNfEGTz2GV8}Ring Ring Ring
VPN连接服务器(这vpn卡了半天进进不去),后过hash认证。要求输入100组abcde满足

乍一看,abcde没限制条件,妙哇,直接爆破,令a=b=c=d,则

上exp
from pwn import *
import string
from hashlib import *
context.log_level='debug'
io=remote('ip',port)
str1=string.digits+string.ascii_letters
io.recvuntil('Please find a string that md5(str + ')
end=io.recvuntil(')')[:-1].decode()
io.recvuntil(' == ')
sha=io.recv(5).decode()
print(end,sha)
def pow(end,sha):
for i in str1:
for j in str1:
for k in str1:
for l in str1:
str2=(i+j+k+l+end).encode()
if md5(str2).hexdigest()[:5]==sha:
return i+j+k+l
v=pow(end,sha)
io.recvuntil('[>] Give me xxxxx:')
io.sendline(v)
for i in range(1,101):
io.recvuntil('[>] a:')
io.sendline(str(i))
io.recvuntil('[>] b:')
io.sendline(str(i))
io.recvuntil('[>] c:')
io.sendline(str(i))
io.recvuntil('[>] d:')
io.sendline(str(i))
io.recvuntil('[>] e:')
io.sendline(str(2*i*i))
io.recvall()flag:GWHT{a_funny_equation}





















