Disabling a User in AD Does Not Disable the User In Lync
However, disabling a user account in Active Directory does not immediately disable the user from using Lync. This is due to the way that Lync performs authentication and, depending on several factors, could result in a disabled user accessing Lync for up to nearly 6 months! Obviously, this is important to understand since you don't want disabled users to access internal resources or make Enterprise Voice calls.
The purpose of this article is to explain how and why this happens and how to successfully disable a Lync user's account immediately without having to delete the user account from AD.
Lync Server 2010 uses several methods of authentication: Kerberos, NTLM, and certificate based. Kerberos is the default authentication method and successful authentication results in the client receiving a Kerberos ticket that's good for 10 hours. Kerberos is used when users are accessing Lync Server while on the domain. NTLM is used for authentication from other locations, such as the Internet for remote access using Lync Edge servers.
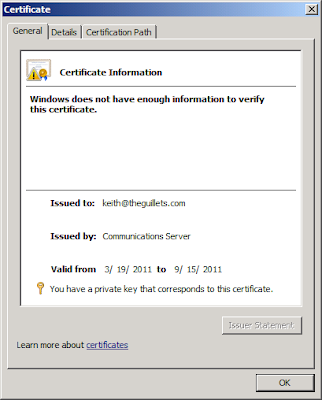
If the user authenticates using one of these two methods and selects the Save my password check box (shown above), the Lync server will generate an X.509 certificate for the user. Lync will publish the certificate to Lync RTC database and distribute it, along with the private key, to the personal certificate store to the user on the local computer. The certificate expires 180 days from the publication date and is used for further authentication for that user from that computer. An example OCS signed certificate from the user's Personal certificate store is shown below:
Certificate authentication is convenient and speeds up the sign-in process significantly, but it means that Lync doesn't check the AD user account to see if it's disabled. If a disabled user signs into Lync using certificate authentication, they will still have access to all Lync features including IM, web conferencing and Enterprise Voice until the certificate expires.
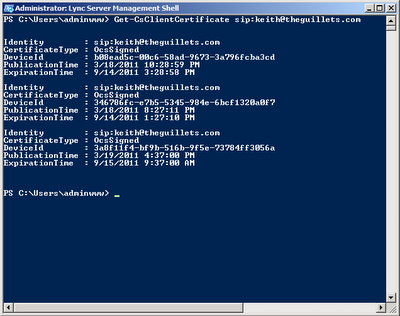
The certificate(s) used by a Lync user can be viewed from the Lync Management Shell using the Get-CsClientCertificate cmdlet. For example,
Get-CsClientCertificate sip:username@domain.comwill display all the certificates the certificates stored in the rtc database for that user. If the user has run Lync from three different computers, there will be three certificates listed for the user, as shown below:
Remote users with a valid client certificate can continue to sign in and access Lync until their certificate expires, regardless of whether their account is disabled or not.
You can revoke a certificate using the Revoke-CsClientCertificate cmdlet in the Lync Management Shell, but this will not affect users who are currently signed into Lync. For domain computers, the user will be able to use Lync until their Kerberos ticket expires (up to 10 hours). Remote users using certificate authentication will remain signed in until they sign out, the Lync server is restarted, or their certificate expires (up to 180 days).
To prevent a user (enabled or disabled) from using Lync, you must disable their Lync account using the Lync Control Panel or the Lync Management Shell, as shown below:
To disable the Lync user account using the Management Shell, run the following cmdlet:
Disable-CsUser sip:user@domain.comNote that it may still take a few minutes for a signed-in user to become disconnected, however they will be unable to access any Lync features, such as new IM, web conferencing, or Enterprise Voice calls immediately. If they happen to be in an IM session or web conference when their Lync account is disabled, they can continue until they disconnect. Likewise, if they are in a voice call when their Lync account is disabled, the call will continue until the call ends. The Lync client for the disabled user will display the following: